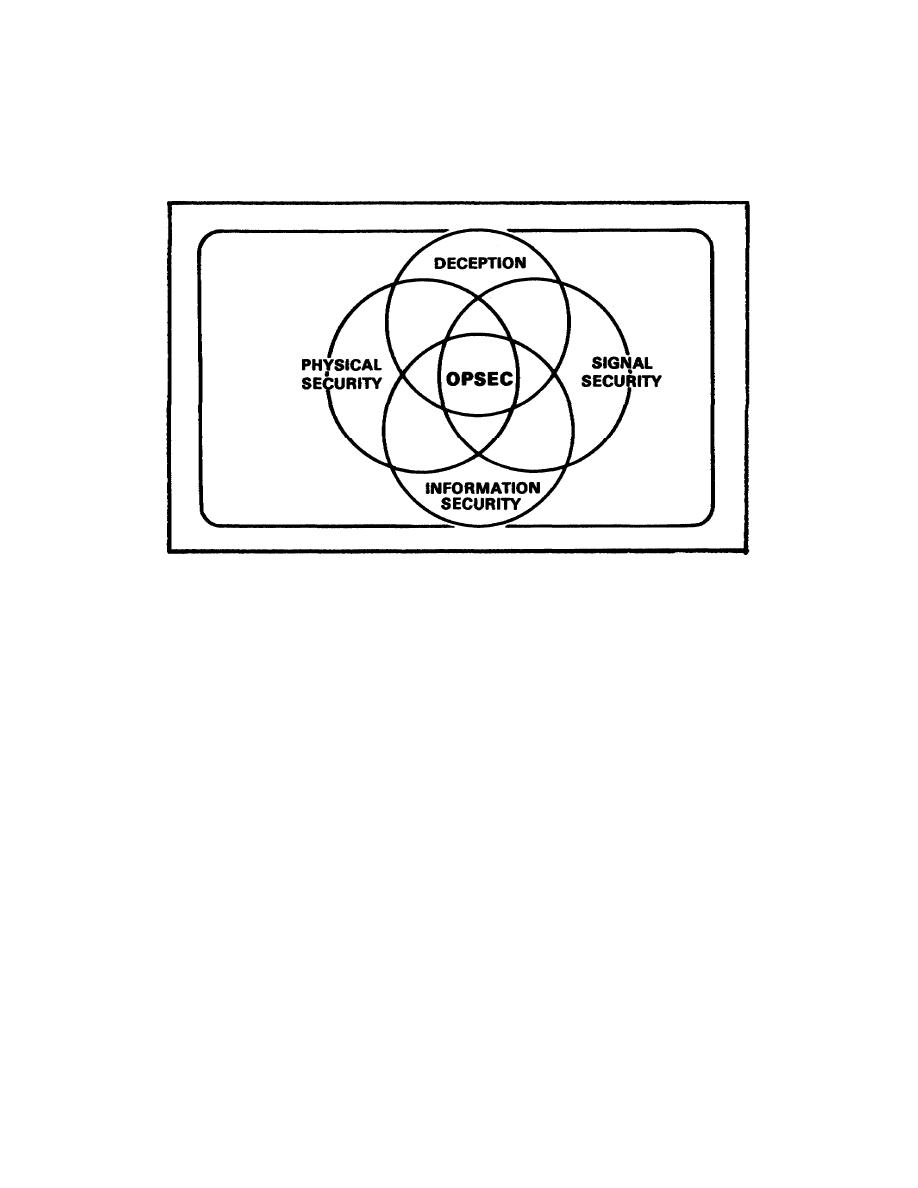
(2) Information Security.
(3) Signal Security.
(4) Deception.
FIGURE 1-1.
OPSEC
c. An
active
OPSEC
program
continually
rates
each
operation.
Evaluation is based upon all known intelligence collection methods.
This
program also assesses vulnerabilities. Then measures are begun to reduce or
negate collection efforts against those areas.
d. OPSEC is the concern of COs, staffs and persons at all levels of
command. Units and individuals set up steps necessary for good OPSEC. In
order to do this, these people must train; they must be able to use proper
techniques and procedures.
OPSEC is a part of all operations.
An
ineffective program results when people do not believe OPSEC is important.
e. The result of a good OPSEC program is force security. Again, this
requires an integrated effort by everyone concerned.
OPSEC is adapted to
fit the operating traits, techniques and needs of each organization. Each
unit takes those steps necessary; these steps should provide security and
retain the element of surprise. The goal of each unit is to keep the enemy
from learning what the friendly unit is going to do.
The intelligence
threat to US military operations today is great, and it continues to grow.
Potential enemies are daily working to gain information.
They seek data
regarding our capabilities and limitations; they want to know our intentions
and plans; they want data on our tactics and readiness.
The enemy finds
certain data valuable and exploitable.
Examples are our communications
patterns and stereotyped
MP1002
1-2



 Previous Page
Previous Page
